We are excited to announce that Bitbucket Cloud event logs now can be tracked in Atlassian Access. With the Atlassian Access audit logs feature, organization admins will ultimately be able to trace critical Bitbucket user activity, including who, when, and what actions were performed.
As part of Atlassian’s cloud-first strategy, Atlassian is investing in building more and more enterprise capabilities into Bitbucket Cloud to ensure a seamless experience for customers looking to migrate from Bitbucket Server to Cloud. This release of audit logs enables admins to have governance around user actions in Bitbucket Cloud. Security teams can use audit logs to investigate incidents, and admins can use them to track down changes in settings or permissions that affect compliance.
Here’s how to enable them for your workspace.
Connect your Bitbucket workspace to Atlassian Admin
These new audit logs are available to Bitbucket customers via Atlassian Access. If you do not already have an Atlassian Access subscription, you can follow the directions here to start a free 30-day trial.
To enable audit logging, start by linking your Bitbucket workspace(s) to your Atlassian organization in Atlassian Admin. This can be done by following the instructions below.
To link a Bitbucket workspace to your organization
- Go to admin.atlassian.com. Select your organization if you have more than one.
- Select Products > … > Link products.
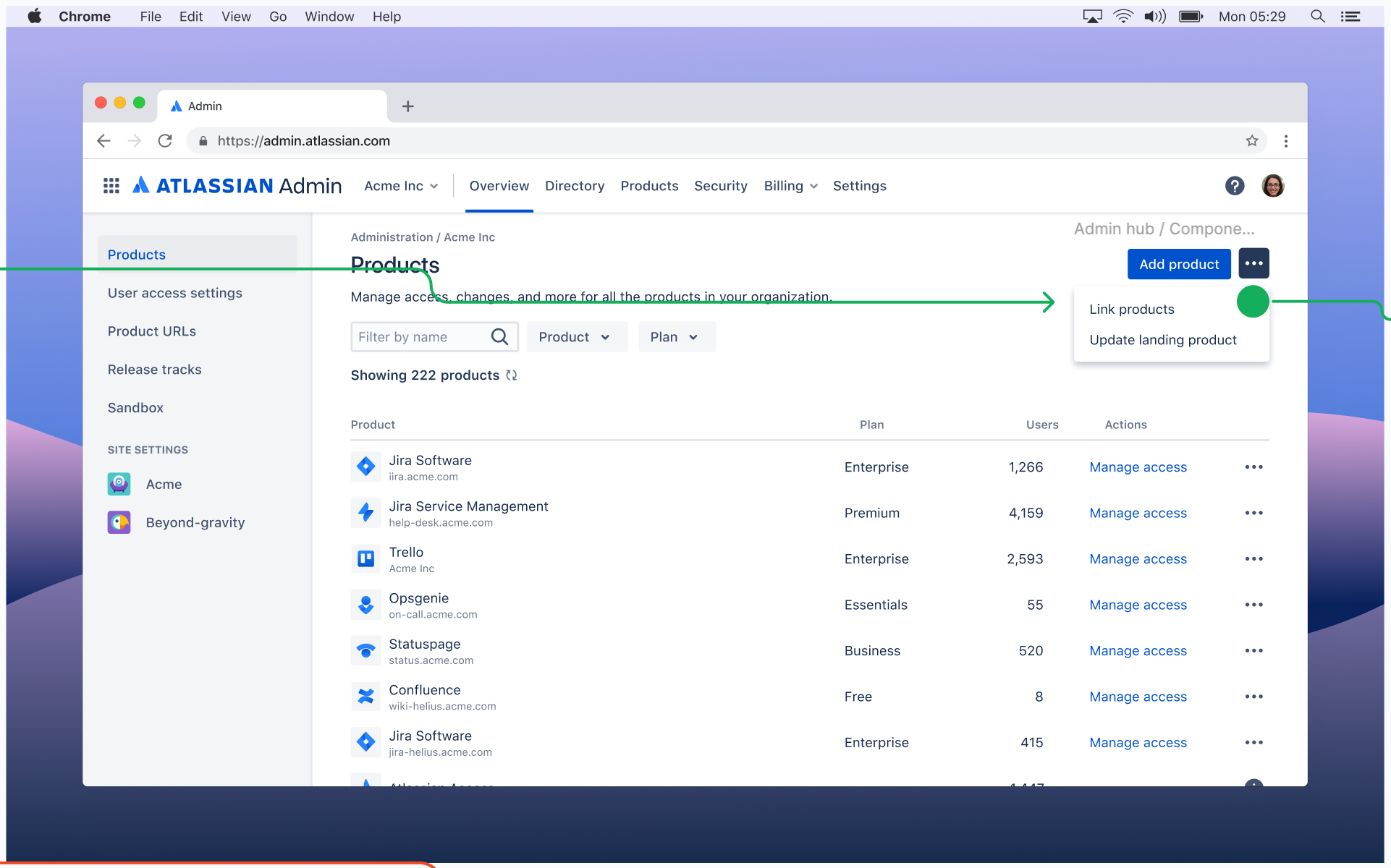
- From the Select products screen, select a Bitbucket workspace you want to link.
- Review and confirm the workspace to be linked.
- Repeat the process for each workspace you want to link.
Once you link a workspace to an organization, you can’t unlink it or transfer it to another organization.
Accessing audit logs
There are two ways to access audit logs, via API and the Atlassian Access UI.
Security teams can use the API to investigate incidents, as well as to import logs into an SIEM tool like Splunk for further monitoring and analysis. More details on the organization audit log API can be found here.
Organization admins can use the UI to search through events to track down changes in settings or permissions that affect compliance, who made them, and when, with the ability to filter by location, actor, or event, as well as to export to CSV.
More information on the organization audit log feature can be found here.
What’s next?
This release covers our first iteration of events, we will continue to roll out additional events over the next weeks to increase coverage. Read more about the events Bitbucket logs here.
Next, we will be tackling more specific user activity, including git activity (for example, clones and commits), to increase coverage of common actions in the product.