As the ownership of application security shifts left into developers’ hands, building security into your CI/CD pipeline is increasingly critical…
This post was written by Sarah Conway from Snyk, our marketplace partner. Find and fix security vulnerabilities faster with the Bitbucket-Snyk integration.
As the ownership of application security shifts left into developers’ hands, building security into your CI/CD pipeline is increasingly critical. When security is automated and adopted early, you’re able to sustain fast development and rapid software delivery. As you look to embed security early and throughout your CI/CD pipeline, these tips will help you improve the security of your Bitbucket deployments, with no workflow interruptions.
1. Never store credentials as code/config
Passwords in your publicly available code can easily get into the wrong hands, which is why it’s best to avoid putting credentials into your repository in the first place. If some do sneak in though, fortunately there are a bunch of great tools available:
- Git-secrets: Statically analyzes your commits via a pre-commit Git Hook to ensure you’re not pushing any passwords or sensitive information into your Bitbucket repository. Commits are rejected if the tool matches any of the configured regular expression patterns that indicate that sensitive information has been stored improperly. This may slow down pushes a tiny bit, but it’s well worth it.
- Vault helps you manage your secrets when in production.
- Keycloak is used for identity and access management in modern applications and services.
- Adaptavist’s ScriptRunner is used as middleware for a more secure approach than injecting credentials via environment variables. This tool helps connect to credential and authentication management systems like Vault and Keycloak.
- GitRob or truffleHog can be used to regularly audit your repos with scans of your codebase to search for sensitive information that might have snuck in via pattern matching.
2. Remove sensitive data from your files and Bitbucket history
It’s best to avoid putting sensitive data in your Bitbucket repository so others aren’t able to see it. But if this does happen, you need to do a number of things to recover. First, invalidate the tokens and passwords that were exposed. Once a secret is public on the internet, you should assume it’s in the hands of attackers and react accordingly.
Next, remove the sensitive data from your repository, but don’t forget that Bitbucket keeps a full history of all your commits. This includes changelogs that list your sensitive information. So it’s important you clear your Bitbucket history after you remove sensitive data from a repo. For more info, see purging files from your repository’s history. Note, while this is a GitHub link, it’s good generic advice for all Git repositories, so you can use these tips in Bitbucket too.
3. Tightly control access
We often focus on complex attack vectors, but fail miserably against some of the simplest ones when securing our applications. For instance, it only takes one developer to leave their password on a sticky note, hanging off their monitor for an attacker to gain access. It’s important to ensure our basic settings and practices are adhered to, both on the Bitbucket platform as well as in general. Mandate the following basic practices for your contributors:
- Require 2-factor-authentication on every contributor’s Bitbucket account.
- Never let Bitbucket users share accounts/passwords.
- Any laptops/devices with access to your source code must be properly secured.
- Repository administrators should manage team access to data. Only give contributors access to the data they need to do their work.
- Bitbucket accounts may be personal accounts, and do not naturally disappear when users leave the company. Make sure you diligently revoke access from Bitbucket users who are no longer working with you.
- Use Bitbucket’s Branch Permissions model to control who can push commits to which branches.
4. Add a SECURITY.md file
It’s natural for most project owners and maintainers to add a README.md for their repository. Likewise, you should include a SECURITY.md file that highlights security related information for your project. This file should include the following:
- Disclosure policy: a process for users to report security issues, e.g. who to contact, where to open a ticket, what info to include in the ticket, etc.
- Security update policy: Explain how you will share details of new vulnerabilities, such as the severity and the risk. This is important for those using your project to run critical applications.
- Security configurations: Provide your project users with suggested settings that should be used with your code, e.g. https, adding an authorization layer, resetting default passwords.
5. Quickly find vulnerabilities within your Bitbucket workflow
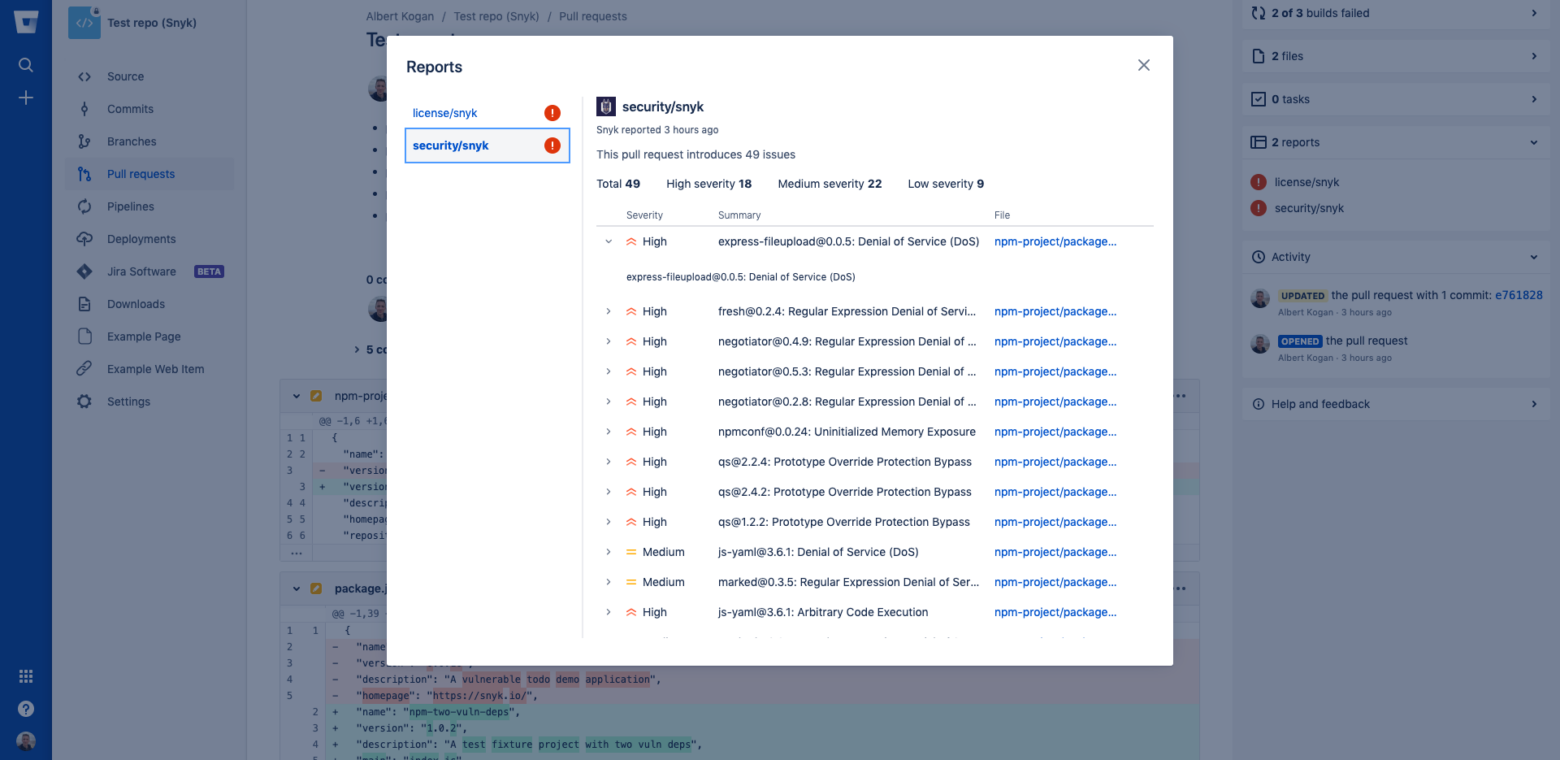
Snyk provides a Bitbucket integration that runs a scan against all opened pull requests to ensure they aren’t introducing new open source vulnerabilities.
If a new vulnerability is found, Snyk alerts you about the newly found vulnerability and opens a fix pull request, including suggested upgrades or Snyk patches to fix the vulnerability.
In Bitbucket’s pull request interface, changes are scanned and results are shown as detailed in-line annotations next to the changes that introduce new issues. These annotations make it easier to understand the results of Snyk’s scan and support informed decisions, as shown below.
Start securing your code
Snyk provides native testing and fixing of open source dependencies that developers can use to automate their workflow through Bitbucket Pipelines. Learn more about the Snyk-Bitbucket integration and sign up for a free starter Snyk plan.