As promised in our blog announcing support for signed commits, you can now use SSH keys to sign commits in Bitbucket Cloud! Signed commits provide an essential layer of protection, allowing developers to verify the authenticity of their contributions using GPG keys – and now SSH keys.
How it works
Here’s a quick reminder of how to enable and use signed commits:
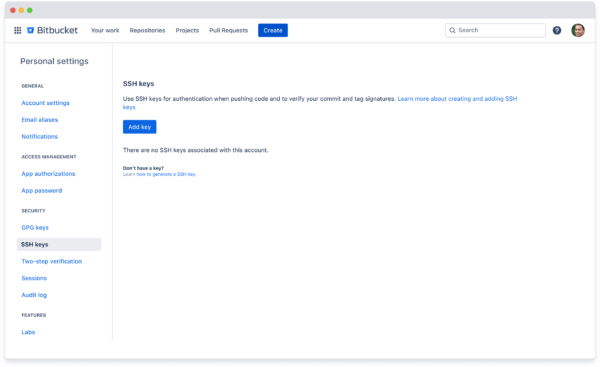
As a developer, you will need to configure your SSH keys within your Personal Bitbucket settings. Add the SSH key associated with your Bitbucket Cloud account email so you can sign your commits with your key.
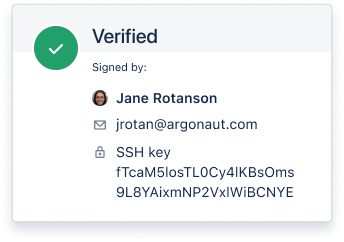
After setting up the SSH key, commits must be signed using the configured key. Bitbucket will validate the signature against the public key and display a ‘Verified’ card for successfully authenticated commits.
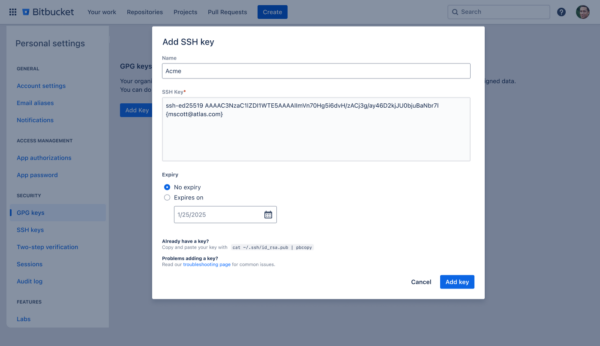
You can also optionally configure an expiration date for your SSH key during set up.
For detailed steps on configuring SSH keys and understanding commit validation statuses, check out our help documentation.
Benefits of enforced signed commits
Repository admins can configure enforced signed commits using SSH keys as well!
We know how important repository integrity is, especially in organizations with strict security and compliance requirements. Enforcing signed commits provides:
- Increased control: Apply consistent security policies across your repositories to meet organizational standards.
- Stronger security: Prevent unauthorized changes by ensuring every commit is verified.
- Better traceability: Know exactly who made changes to your codebase and ensure all contributions are authentic.
Want to ensure every commit to your repositories is signed? To create and enforce signed commits within a workspace or project, you will need to upgrade to a Premium account.
What’s next?
We’ll continue to add new capabilities, such as introducing system-signed commits. These improvements will help address specific use cases, like merges and commits made through the Bitbucket UI. Stay tuned for more updates!
