Getting Started with Atlassian Guard
Use this detailed step-by-step guide to set up your Atlassian Guard trial
Introduction
In this setup guide, we’ll walk you through the steps for setting up your Atlassian Guard trial. This guide includes steps that follow our best practice recommendations, but some controls may not be needed for your organization’s unique requirements.
Getting started
Start protecting your business with these three steps to gain visibility into your organization and effectively manage access for your users.
Important before you start
Atlassian Guard is implemented across all Atlassian Cloud products. Before you verify your domain and set up an organization, make sure stakeholders, admins, and teams using Atlassian cloud products are made aware.
1. Confirm or verify your domain: Verifying your domain(s) proves you own it and allows you to take control of your accounts. Confirm or create your organization by going to admin.atlasssian.com.
2. Claim your accounts: Streamline your user management with managed accounts. Claiming accounts allows you to manage users more efficiently and apply security settings automatically and at scale.
3. Start your 30-day trial to setup Atlassian Guard features.
Organization and domain verification
What is an Atlassian Organization?
An Organization is a management layer that gives admins the ability to view and apply controls to all Atlassian accounts using an email address belonging to their company. It is the top of a company’s Atlassian cloud hierarchy, where all users and content are centrally managed. All Atlassian sites and products are listed in the Organization, providing a full picture of the company’s Atlassian cloud landscape. You can access your Organization at admin.atlassian.com.
What is domain verification?
Domain verification is the process by which an organization admin can begin centrally managing all of the Atlassian accounts that utilize the company's domain. Administrators that can edit their domain’s DNS or HTTPS settings can verify their company’s domain with Atlassian Guard.
How does domain verification work?
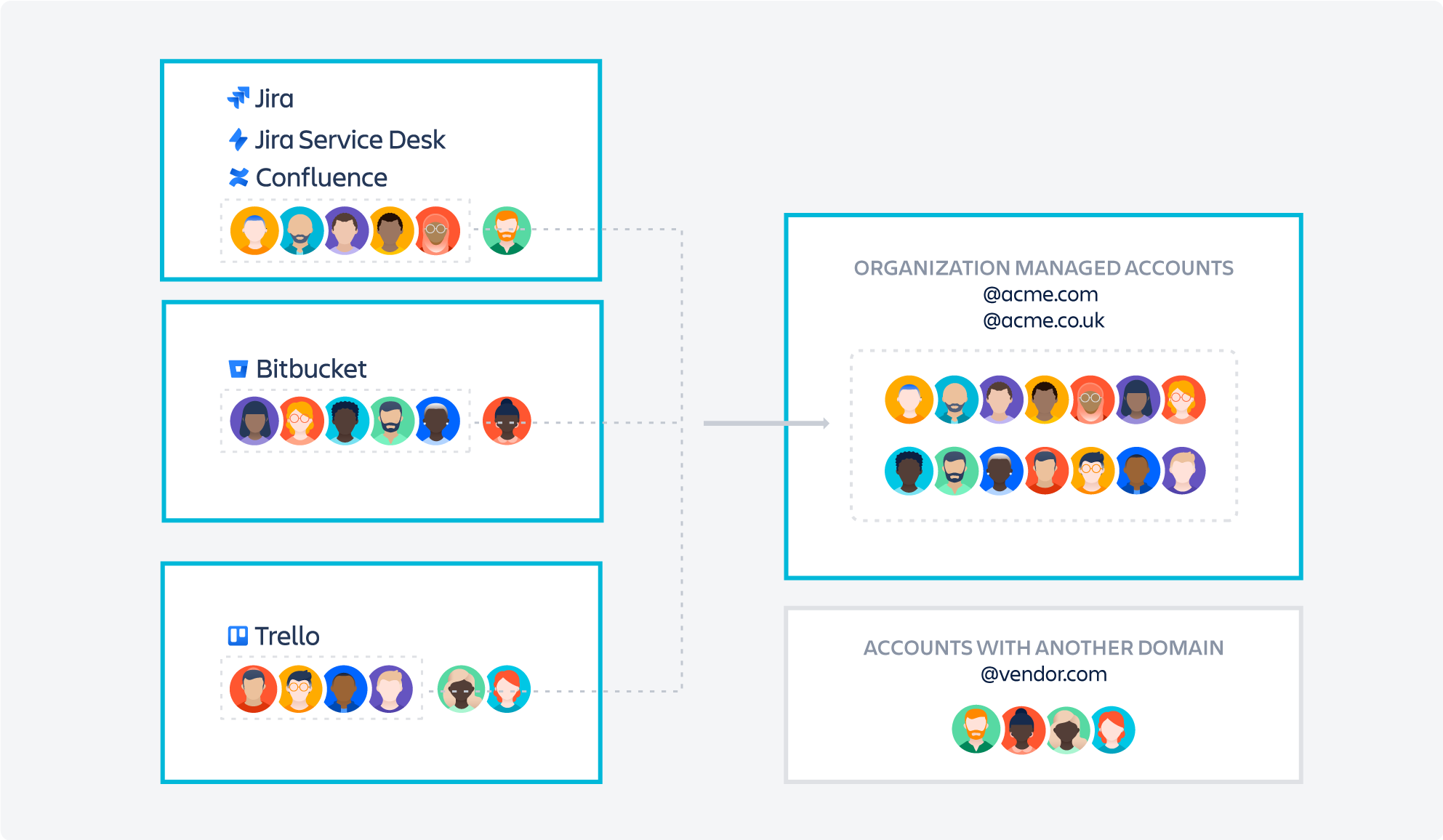
Imagine your company is called Acme Inc. and it owns the “acme.com” and “acme.co.uk” domains.
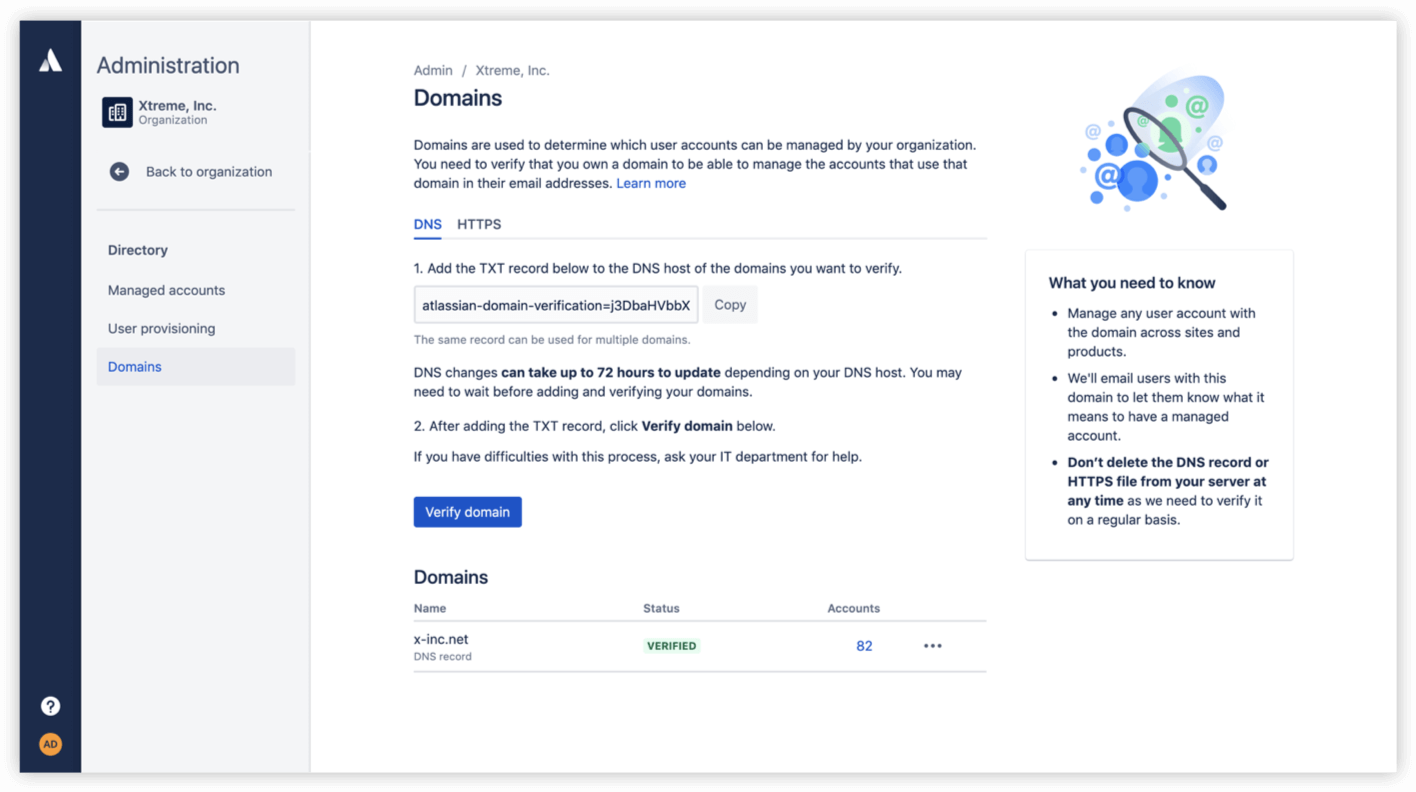
Once you have set up an Organization, you can verify ownership of those domains from the Directory > Domains page in the organization view. You can either upload an HTML file to the root folder of your domain's website, or copy a TXT record to your domain name system (DNS).
After one of those steps, you can click Verify. Atlassian cloud users who have set up their accounts under emails from those domains, like “jack@acme.com” and “jill@acme.co.uk”, will now be managed as part of your Organization.
Understand that when you verify your domain, you may begin managing Atlassian accounts for sites and products that you don't currently manage. For example, there might be other teams or employees within the company who have signed up for Atlassian cloud products and weren't previously within your purview. Before you verify your domain, we recommend that you check in with other site admins or teams within the company using Atlassian cloud products, so they are aware of the upcoming changes.
Once an administrator from an organization verifies their domain, Atlassian users with email addresses belonging to that domain will see a message in their profile settings that their account is now managed by their organization.
You can go to the managed accounts page of your organization and edit user details for individual accounts. If you want to apply security policies and subscribe to Atlassian Guard, your users with managed accounts will be subject to any policies you set.
SAML Single Sign-on
What is SAML SSO?
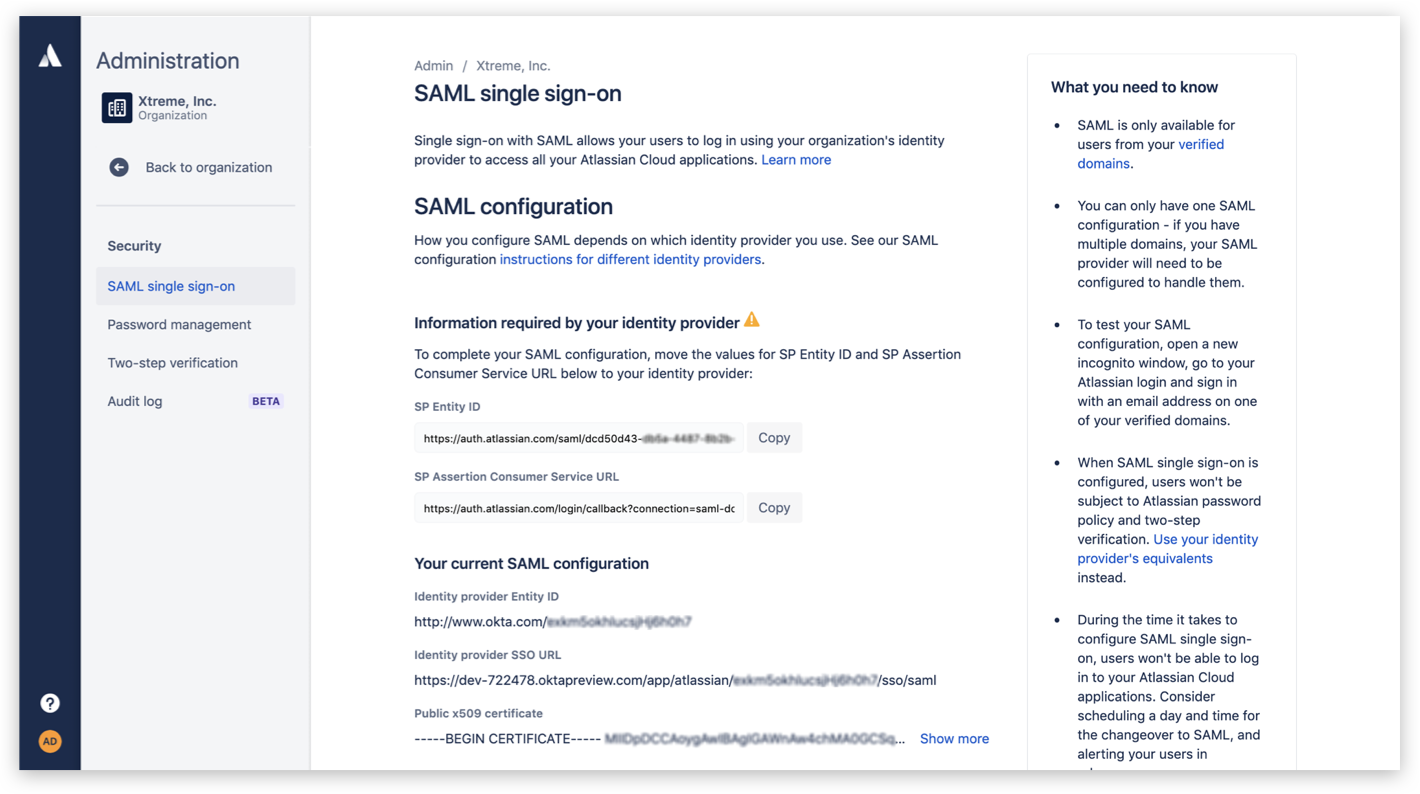
SAML single sign-on (SSO) allows your users to authenticate to Atlassian cloud products through your company's existing identity provider. This means they can access multiple tools with the same set of credentials, while using a more secure method of authentication than just a user name and password.
Why use SAML SSO?
SAML SSO provides employees and customers with a simpler, easier process for accessing the tools they use, and allows admins to enforce identity-related security controls at scale, making the task of securing large groups of users far simpler.
How it works
Atlassian Guard integrates with your company’s identity provider to provide a simple, seamless authentication process for employees and customers to access Atlassian cloud products.
SCIM automated user provisioning
What is user provisioning and de-provisioning?
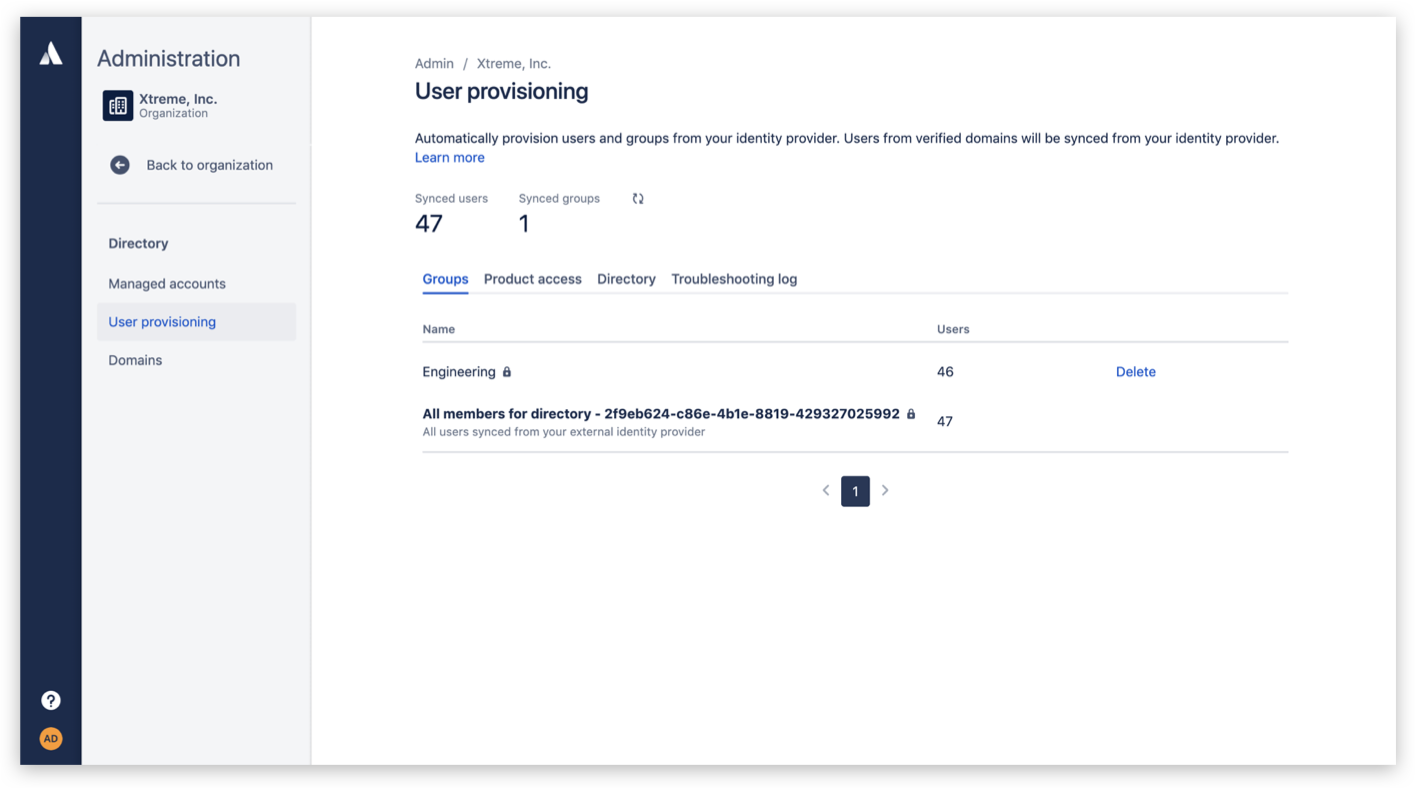
With user provisioning and de-provisioning, access to Atlassian cloud products will be defined by rules set in your external directory. Onboarding and offboarding of users happens automatically whenever a user is added or removed from your external directory. This user directory is usually provided as a service by a software vendor called an identity provider. Atlassian Guard allows customers to integrate their Atlassian cloud products with an identity provider.
Why implement user provisioning and de-provisioning?
User provisioning reduces the manual work involved with granting employees application access when they join the company or move to a new team. In addition, automated de-provisioning reduces the risk of information breaches by removing access for those that leave the company. And since user accounts are automatically removed when people leave the company or a group, costs are more tightly controlled.
How it works
Atlassian Guard integrates your user directory with your Atlassian cloud products, and automatically syncs updates you make in your identity provider with users in your Atlassian organization.
When a new employee joins the company, perhaps the engineering team, the IT admin typically needs to give this new employee access to at least 10 different apps that engineers typically use to do their jobs. With user provisioning set up, the admin just needs to add the employee to the engineering group once, and all the apps they need will be automatically provisioned for that user. If the engineer leaves the company, the admin just needs to make one change in their user directory, and access is revoked.
If an employee switches teams, say from engineering into product, they might need access to a slightly different toolset. All the admin needs to do is make one change in their user directory group settings, and access is revoked to the tools they no longer need and granted to the new ones.
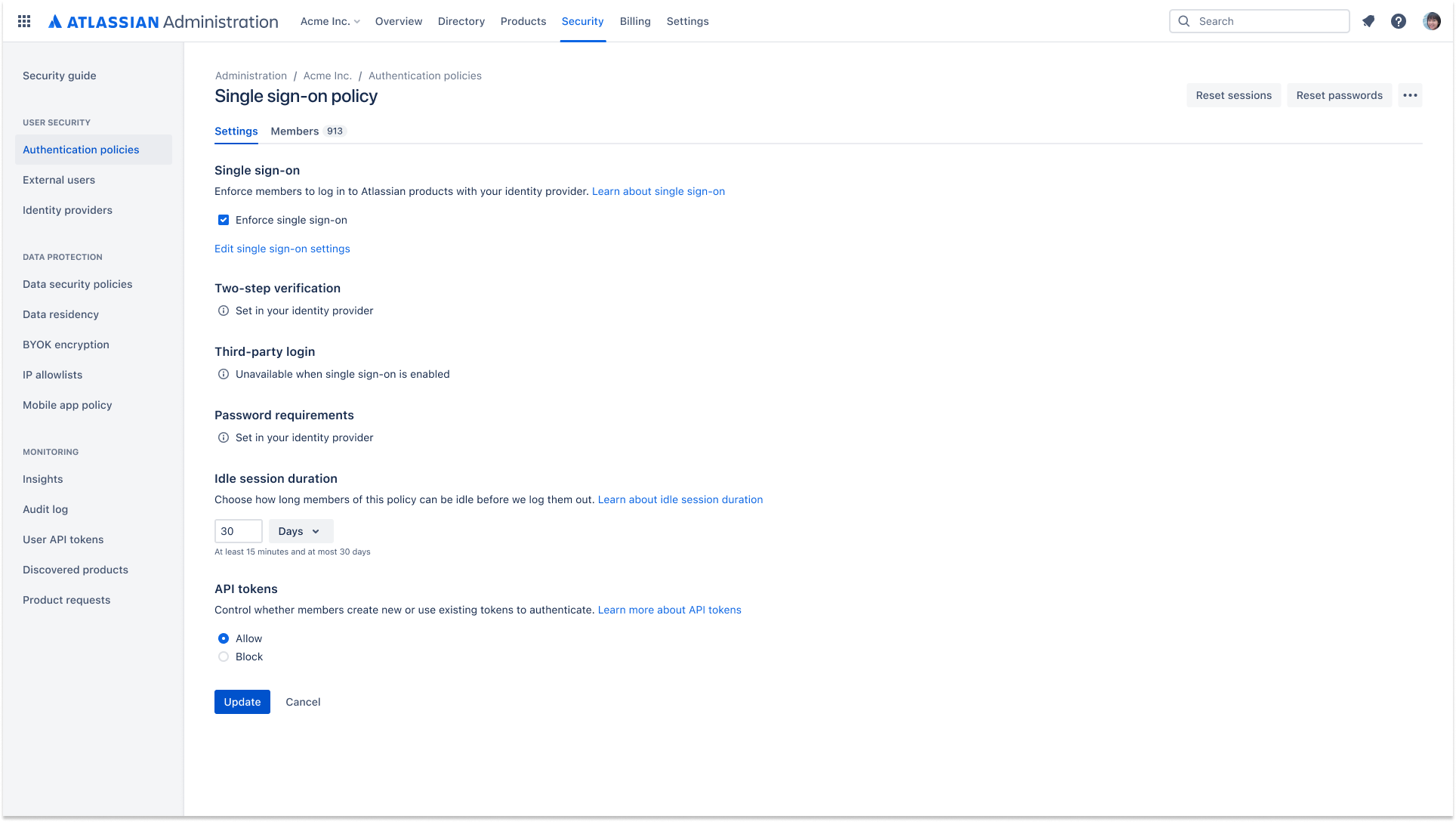
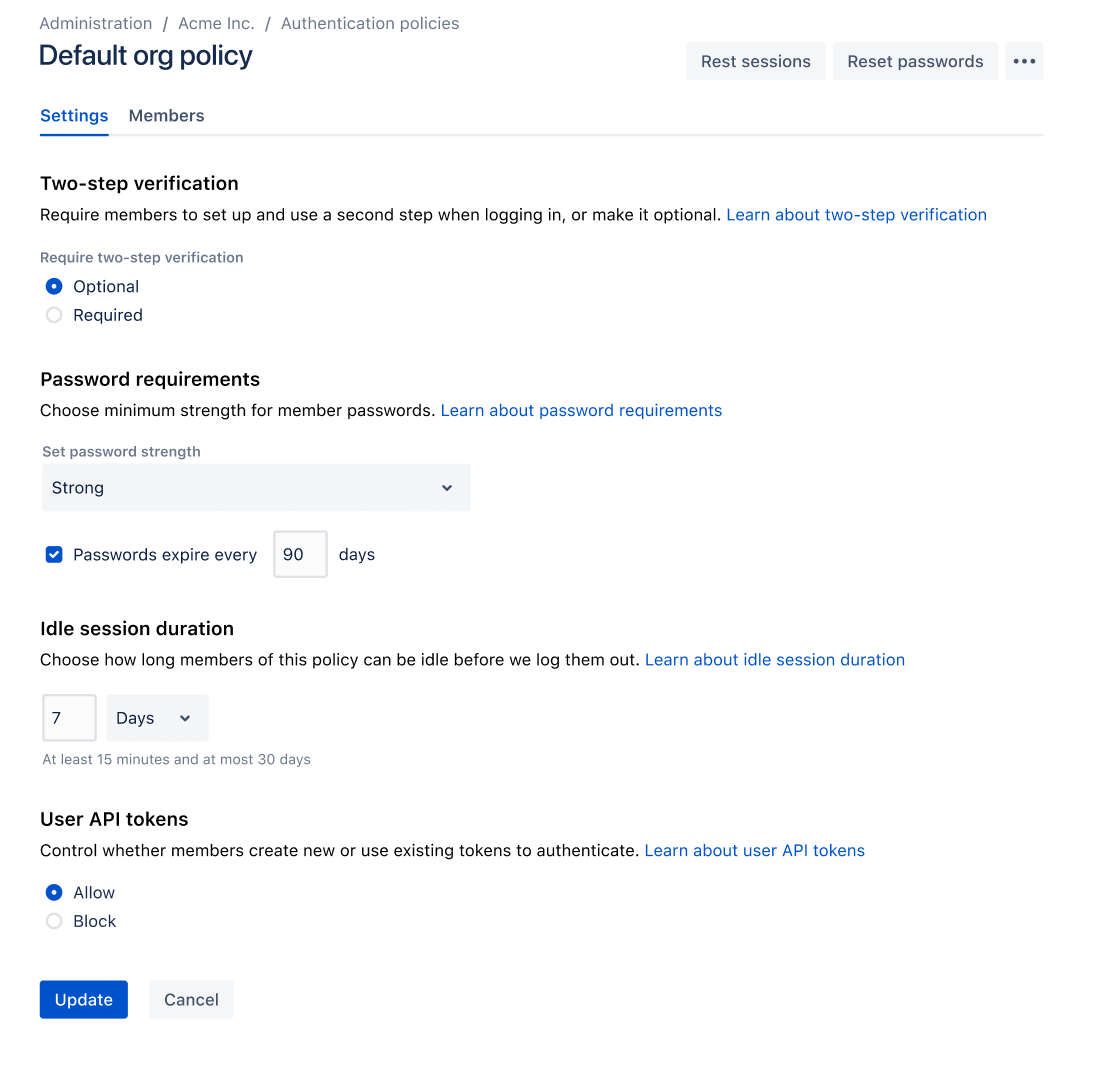
Defining multiple authentication policies
What are authentication policies?
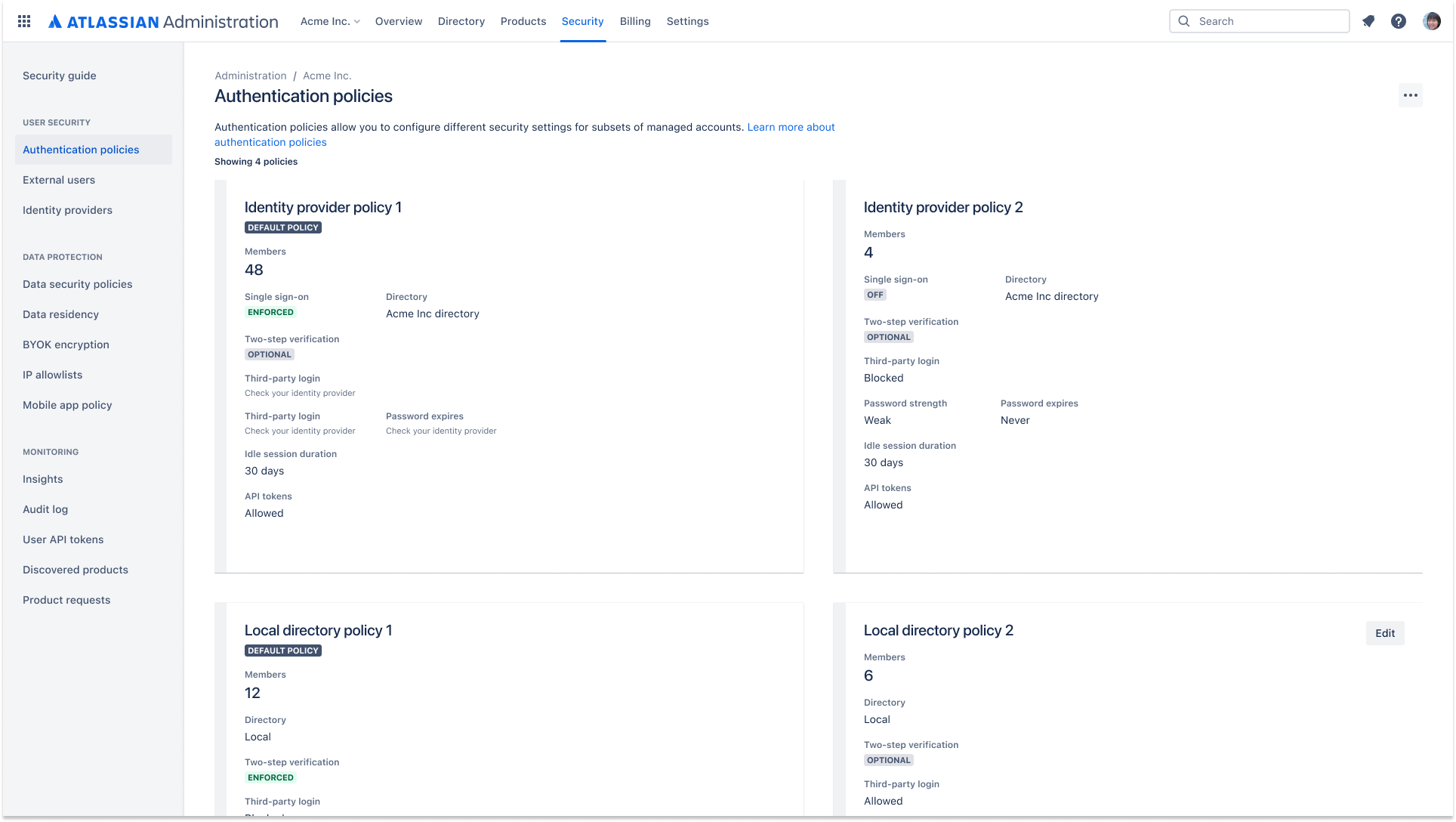
Admins can set authentication policies with managed accounts and apply the authentication settings to members.
The authentication settings that can be configured through policies are:
- single sign-on (SSO)
- enforced two-step verification (2SV)
- password policies (password strength, password expiry)
- session duration
Why apply multiple authentication policies?
There are many reasons to have multiple authentication policies within an organization and the main ones are to:
- designate policies to specific user subsets
- test authentication setting functionality
How it works
Admins have the flexibility to define multiple authentication policies and apply them to different subsets of users in the organization to ensure each set of users have the appropriate level of security.
A separate authentication policy can be set up to test a SAML configuration by enabling single sign-on for a small test group before rolling it out to the whole organization.
Enforced two-step verification
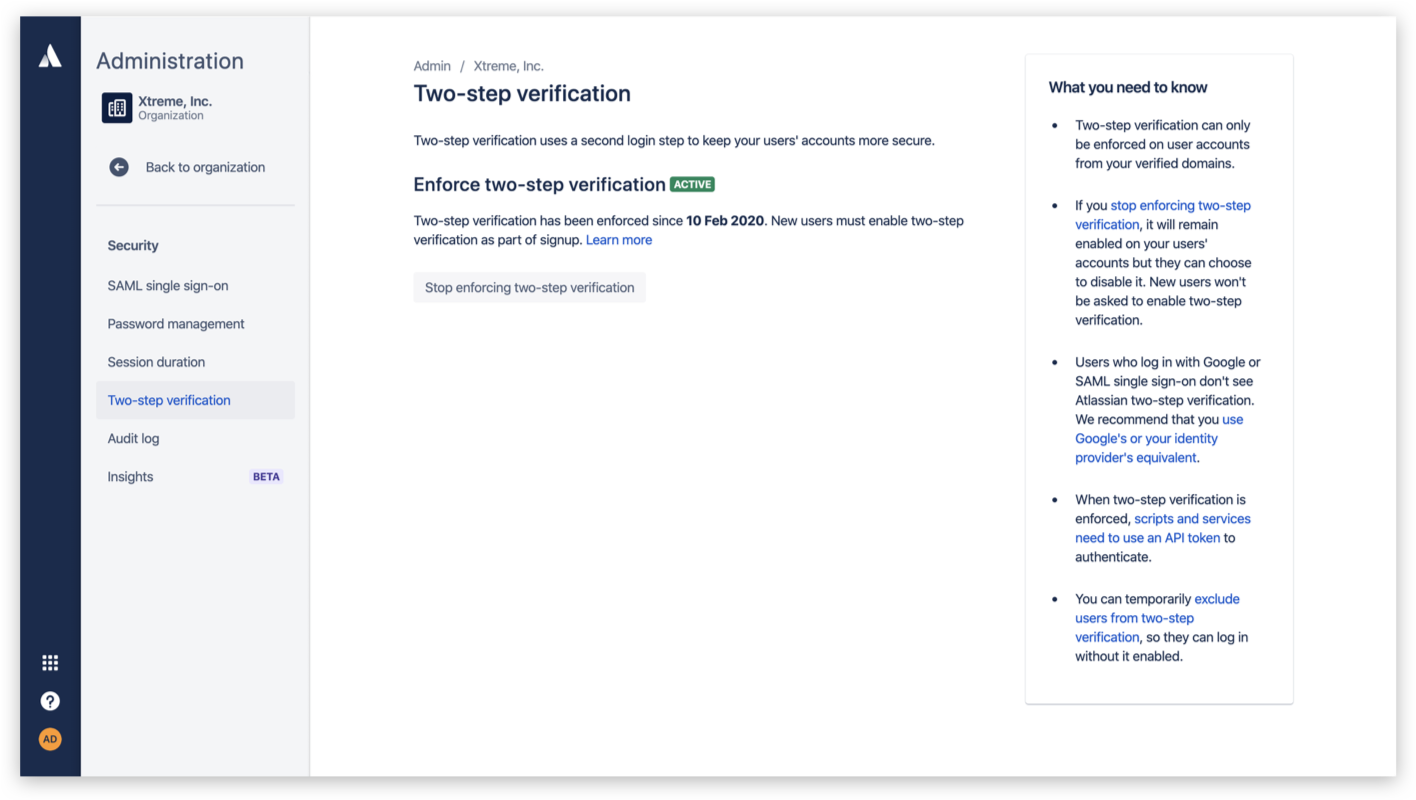
What is enforced two-step verification?
Enforced two-step verification is a security policy that requires the users in an organization to turn on two-step verification in order to log in and access their Atlassian cloud products.
Why use enforced two-step verification?
Enforced two-step verification keeps accounts secure if the password to the account is compromised, improving the security of the information accessible by those accounts.
How it works
If someone already has an existing Atlassian account when enforced two-step verification is applied, they will be logged out of their account and prompted to set up a secondary verification method the next time they log in. If someone is setting up an Atlassian account for the first time, they will be required to set up a secondary verification method as part of the onboarding flow.
API token controls
What are API token controls?
API tokens allow a user to authenticate with cloud apps to retrieve data from the instance through REST APIs. Token controls enable admins to view and revoke the use of API tokens by their managed and external users.
Why use API token controls?
User API token controls provide admins with greater visibility and control over the user API token lifecycle, which improves their organization’s security posture. This includes:
- Greater control over which users can access data via an API token
- Greater visibility into which users are creating and revoking API tokens, allowing them to identify and address security threats resulting from bad actors
Learn how users can create and use an API token in Atlassian
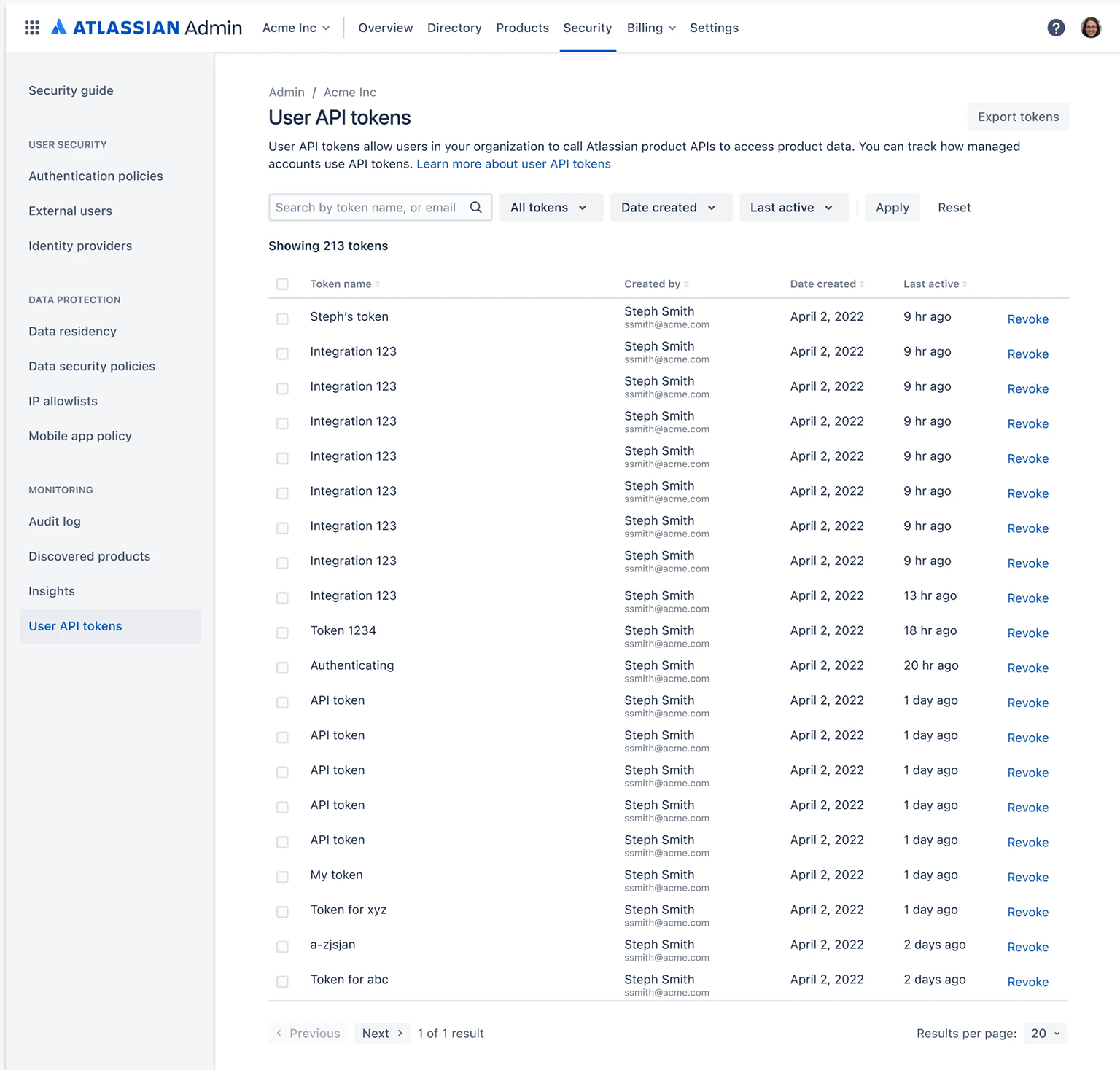
How it works
Admins can control whether managed users are allowed to create new user API tokens or use existing tokens by navigating to the API tokens setting under Authentication policies.
Admins are also able to view all active user API tokens associated with managed accounts within their organization in Atlassian Administration. This makes it easier for them to navigate to a specific user’s account details in managed accounts if they wish to revoke access.
Control whether users can authenticate with a user API token
View all active user API tokens for managed accounts
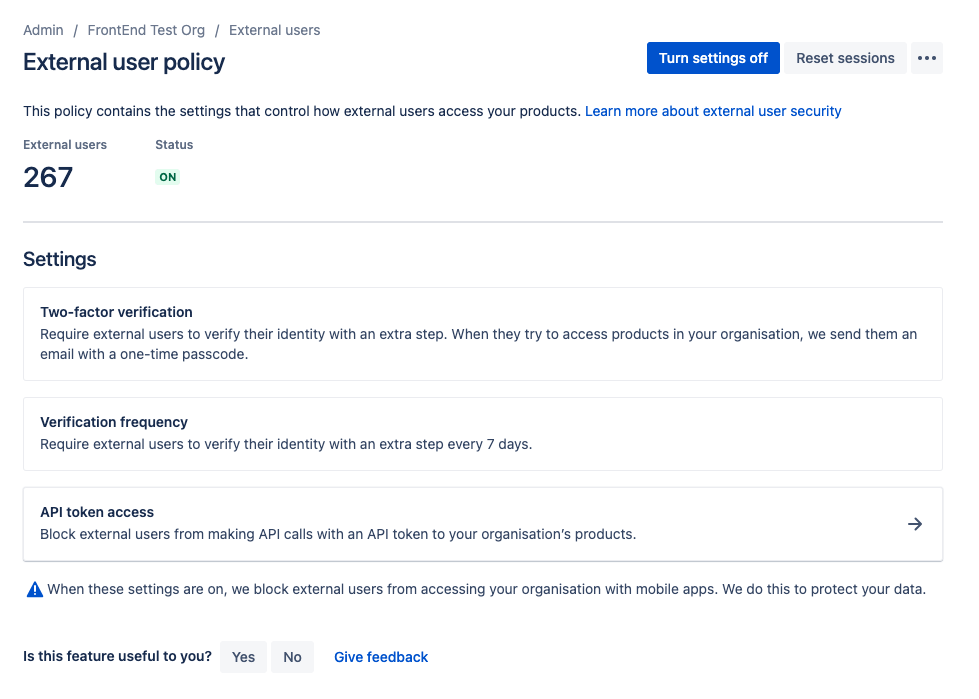
Allow or block external users from accessing API tokens
Mobile app management (MAM)
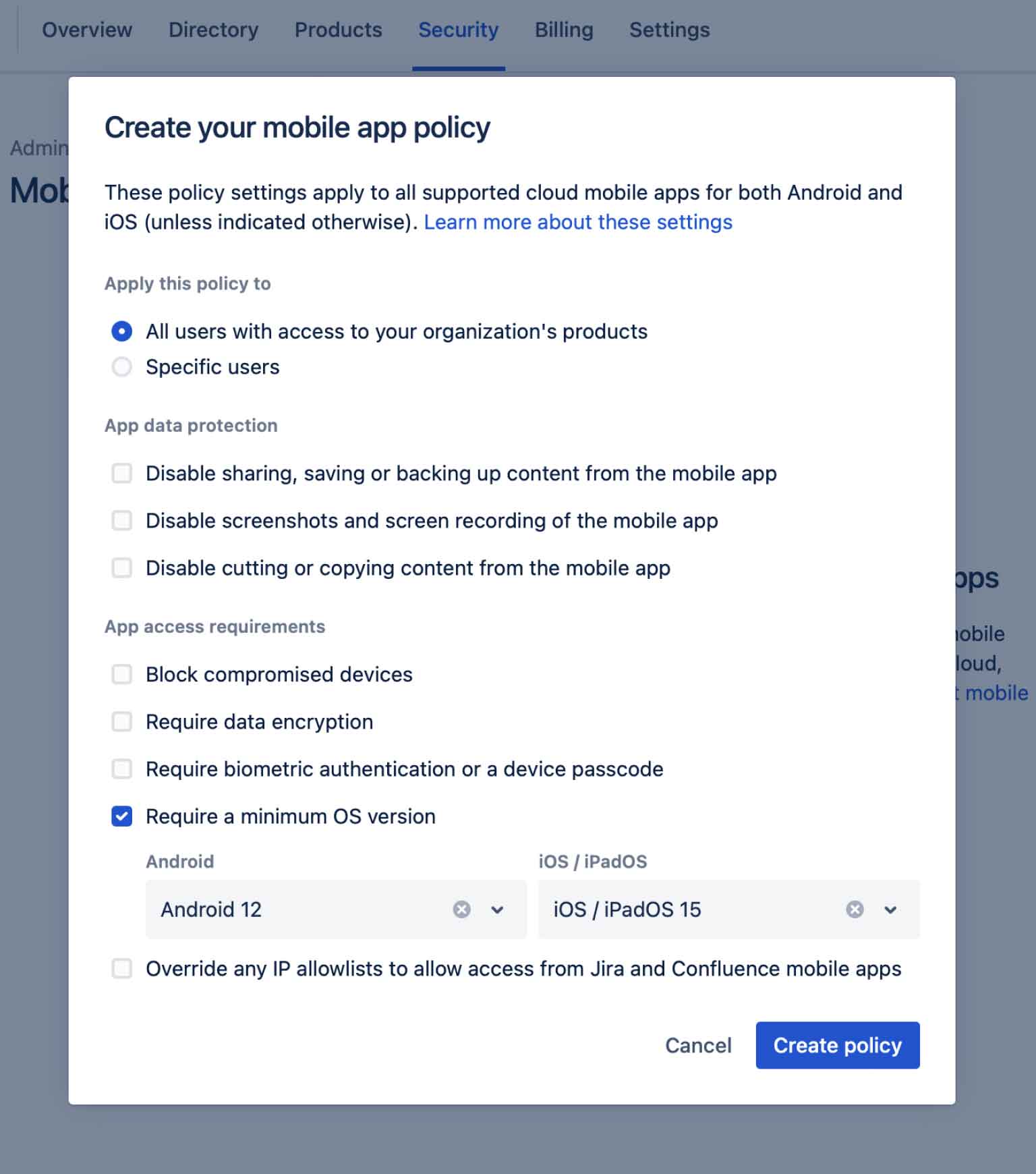
What is a mobile app policy?
Enable greater flexibility across your organization with Mobile App Management (or MAM). MAM allows you to configure security controls for bring-your-own-devices (BYOD) across Jira Cloud, Confluence Cloud, and Opsgenie mobile apps.
Why use a mobile app policy?
Implementing a mobile app policy helps your organization enable collaboration while proactively setting controls to protect users and data. When you set up a mobile policy, your users' devices will need to meet your security requirements before they can access the mobile apps connected to your organization.
How it works
A MAM policy can be applied to all users or a specific subset of managed users. MAM is available for both managed and external users. Your organization can create an additional layer of protection with MAM features, including:
- Disable sharing, saving or backing up content
- Disable screenshots and screen recording
- Disable cutting or copying content
- Block comprised devises
- Require data encryption, biometric authentication, or a device passcode
- Require a minimum OS version
- Override any IP allowlists to allow access from Jira and Confluence mobile apps
Automatic product discovery
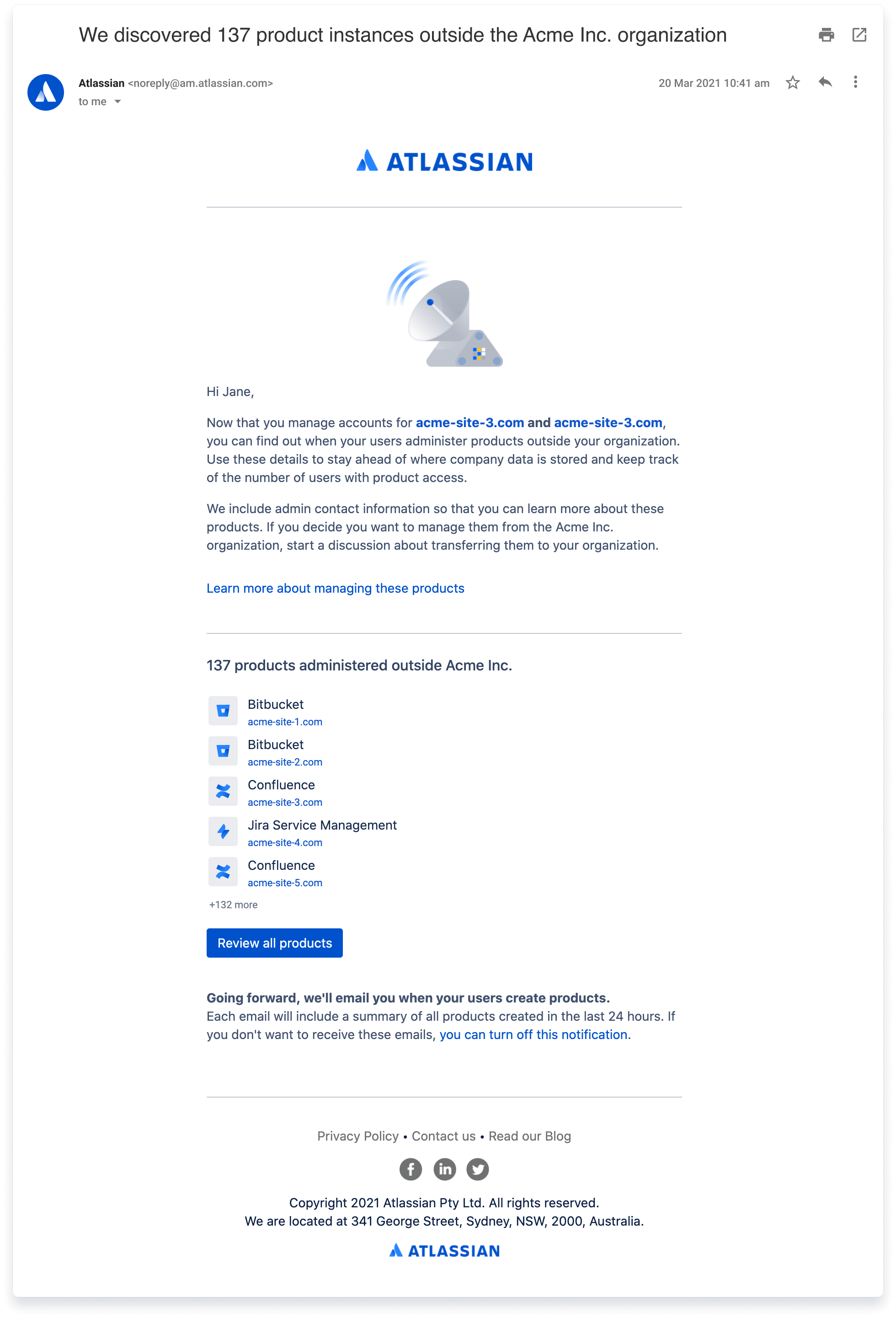
What is automatic product discovery?
Admins gain visibility into and can manage shadow IT at their organization by discovering Atlassian cloud products their managed users created, seeing who the administrator of these products are, and how many users have joined those products.
Why does automatic product discovery matter?
In the cloud, users can easily create new products whether or not the organization’s central admin team is aware or approves of it. This can be a scary thing for admins as it can lead to:
- lack of cost control
- operational complexity
- security and compliance concerns
Automatic product discovery allows organization admins to gain consistent visibility into user-created Atlassian cloud products (shadow IT) that exist within their organization. It also helps make these shadow IT products easier to manage by connecting organization admins with the users who administer these products. By reaching out to the owners of the shadow IT, organization admins can start to:
- mitigate billing and security concerns by removing the product(s)
- create an IT-approved product that meets user needs
- consolidate products and data into the organization’s official product
How it works
Atlassian will proactively send an email with the number of shadow IT products created by their managed users and what the exact shadow IT product is.
Within “admin.atlassian.com”, organization admins can also view additional information, such as the owner of these products, how many users are in that product, and the date it was created.
To start remediation, organization admins can click on the "…" eclipses to contact the product owner.
Organization-wide audit logs
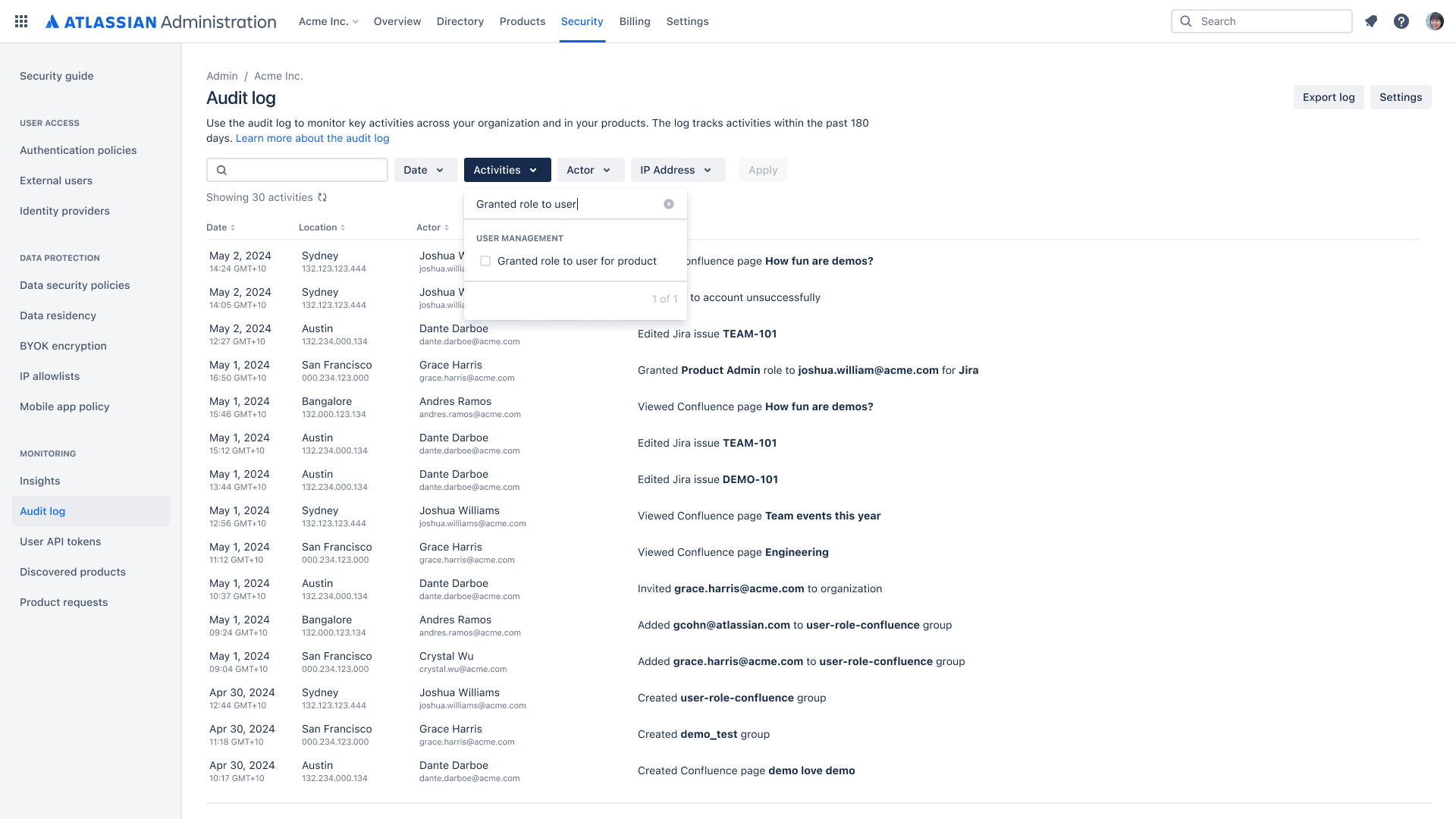
What is an organization audit log?
Organization insights allow admins to track the adoption of their Atlassian products and evaluate their users' security posture. The feature provides a set of analytics across Jira and Confluence cloud products that are linked to an organization.
Why use an organization audit log?
Data loss prevention: By seeing exactly who was given access to which product instance, admins can take action to shut off that user’s access and get a detailed record of suspicious activity in the event of data loss (e.g., intellectual property, sensitive healthcare or financial data) to immediately take remedial action.
Activity monitoring: In a troubleshooting or root cause analysis scenario, admins can immediately see who and when users were given access to help identify what may be related to an issue that occurred at specific times. This is especially useful for compliance and auditing purposes.
Collaboration control: Information from the audit log answers questions like “Is that user supposed to be reading or editing that page or project?” so that they can be removed, or “How did this user lose access to a product that he/she should have access to?” so that access can be restored.
How it works
Within the Atlassian Guard dashboards, organization administrators can view and filter the audit log. Admins can also download the past six months of activity for export into a .CSV file.
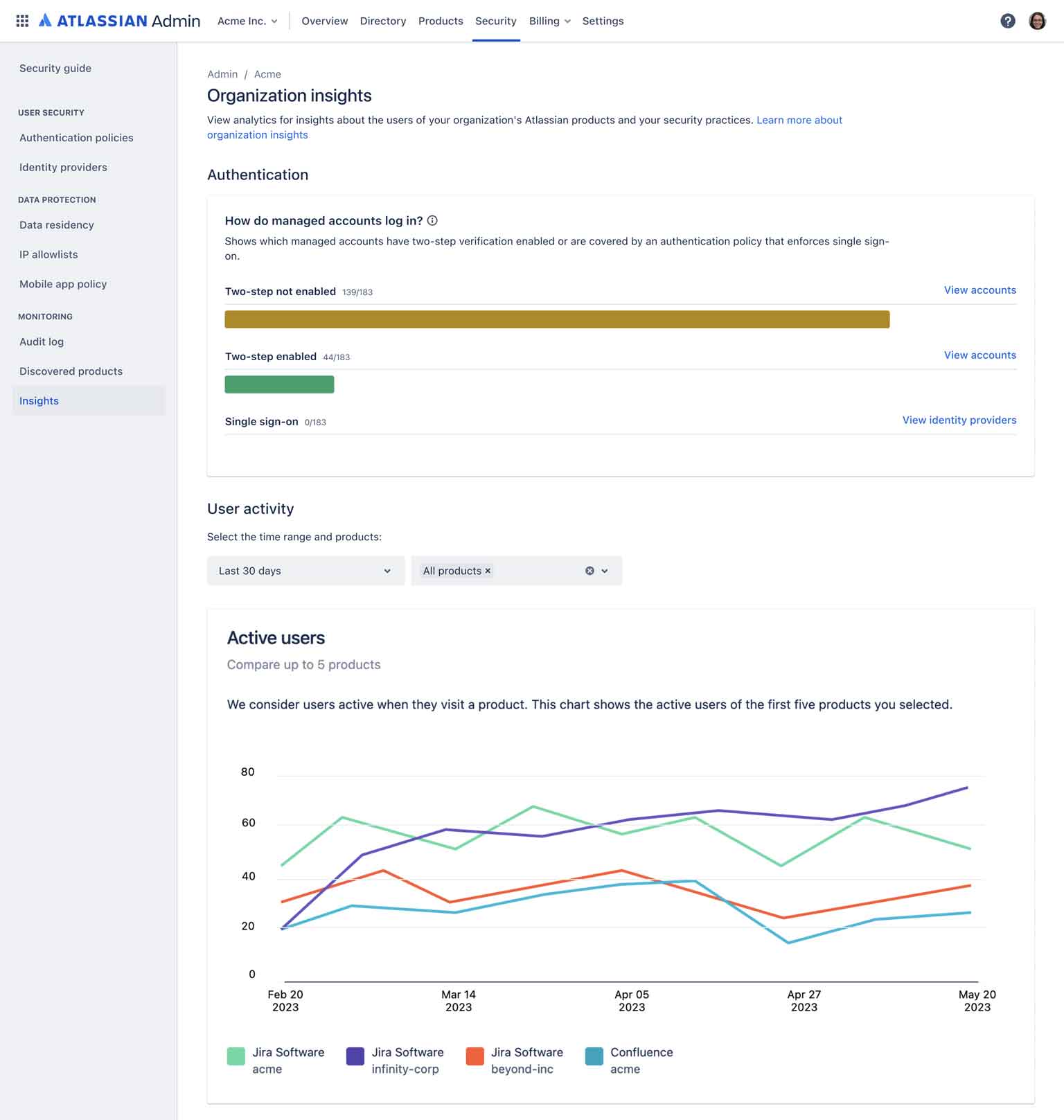
Organization-wide insights
What is an organization insights?
Organization insights allow admins to track the adoption of their Atlassian products and evaluate their users' security posture. The feature provides a set of analytics across Jira and Confluence cloud products that are linked to an organization.
Why use organization insights?
Admins can achieve better visibility into the usage of their Atlassian products and make more data-driven decisions when it comes to increasing adoption or optimizing their products' ROI. In addition, admins can view the security posture of their users at a glance, which helps admins become more proactive in administering users and permissions.
How it works
Admins can access organization insights from the Security section of the organization administration hub. On this page, admins can:
- View daily and monthly active users across Jira or Confluence cloud products linked to their organization
- Review current license usage to better understand their Atlassian spend
- See how many managed users have two-step verification or SSO enabled
We will continue to add more insights to provide admins visibility into security posture and usage at the organizational level.
CASB integration with McAfee MVISION Cloud
What is a CASB?
A Cloud Access Security Broker (CASB) is a third-party software that provides advanced cloud security functionality by integrating with cloud products used in an organization. The CASB software tracks and analyzes all information sent and received by each cloud product. With this data, CASB vendors provide greater visibility, remediation, threat protection, policy management, and data security.
Why use a CASB with Atlassian Guard?
Through the integration between the CASB software McAfee MVISION Cloud and Atlassian Guard, admins gain:
- centralized visibility into content and user actions across cloud services, including Atlassian cloud products
- greater ability to protect important Atlassian cloud data wherever it lives
- increased protection from threats through suspicious activity monitoring
With Atlassian Guard, McAfee MVISION Cloud captures a complete record of Atlassian organization-level activities and leverages machine learning to analyze activity to accurately detect threats.
How it works
Centralize governance of your Atlassian cloud products with Atlassian Guard then connect to the CASB software McAfee MVISION Cloud to get automatic security monitoring and behavioral analytics through your McAfee MVISION Cloud dashboard.
What’s next?
Congratulations! You’ve successfully setup Atlassian Guard for your organization. You’re one step closer to effectively preventing unauthorized access and risky behavior across your Atlassian Cloud products. Be sure to subscribe to continue using the features of Atlassian Guard after your trial.
How does Atlassian Guard pricing work?
We offer flexible pricing per unique user. A unique user for Atlassian Guard means that regardless of how many products a user has access to, they count as a single user for billing.
Our pricing ensures you receive the most value from your Atlassian Guard subscription as your organization grows. As you add more users, the average price per user will decrease.
Each billing cycle (either monthly or annually), we’ll charge you for the number of unique users provisioned to a product supported by Atlassian Guard, regardless of how many products any one user has access to.
That means a user provisioned to both Confluence and Jira only counts as a single user when we bill for Atlassian Guard.
Still need help?
Our team can answer all of your questions about Atlassian Guard set up and more
Before you get started
Atlassian Guard is implemented company-wide and requires coordination between stakeholders, such as other admins, across your organization.
Before you set up an organization and verify a domain, make sure any other teams using Atlassian cloud products are aware of the upcoming changes.
Getting started
1
Confirm or create your organization by going to admin.atlassian.com
2
Add users to your organization by verifying domain(s) that your company owns.
3
Start your 30-day trial to set up Atlassian Guard features.
Feature details
Once you verify your organization’s domain(s) and start a trial, you can enable features in the admin console.
The chapters below describe how each feature secures your organization.
Read more
Atlassian Trust Center
Learn about reliability, privacy, and compliance at Atlassian
Atlassian Community
Discuss, ask, and learn all things Atlassian Guard in the Community
Resources
Explore more materials on cloud security and scale